Before going to Distance Protection First see what is Protection System in Power System & Transmission Lines.
- The purpose of protective relays and system is to operate the correct CB so as to disconnect only the faulty Equipment/Ckt. From the system as quickly as possible, Thus minimizing the trouble & damage caused by fault when they do occur.
- Most faults are shunt faults which are characterize by increase in current, reduction in voltage, power factor & frequency.
Primary & Backup Protection
- Primary relaying or also called Group-1, Main-1 or Stage-1, the function of this is first line of defense for protecting the eq. whereas the backup relaying (Group-2, Main-2 or Stage-2) works only when primary relaying fails.
- Time delay and relay settings of backup relays are higher than the primary relays.
- In distance protection Characteristics are also different for both primary & backup relays.
Understanding Distance Protection
Why Distance Protection
> Since the impedance of a transmission line is proportional to its length, for distance measurement it is appropriate to use a relay capable of measuring the impedance of a line up to a predetermined point (the reach point). Such a relay is described as a distance relay and is designed to operate only for faults occurring between the relay location and the selected reach point, thus giving discrimination for faults that may occur in different line sections.
> The basic principle of distance protection involves the division of the voltage at the relaying point by the measured current. The apparent impedance so calculated is compared with the reach point impedance.
If the measured impedance is less than the reach point impedance, it is assumed that a fault exists on the line between the relay and the reach point. The reach point of a relay is the point along the line impedance locus that is intersected by the boundary characteristic of the relay. Since this is dependent on the ratio of voltage and current and the phase angle between them, it may be plotted on an R/X diagram. The loci of power system impedances as seen by the relay during faults, power swings and load variations may be plotted on the same diagram and in this manner the performance of the relay in the presence of system faults.
DISTANCE RELAY CHARACTERISTICS
Some numerical relays measure the absolute fault impedance and then determine whether operation is required according to impedance boundaries defined on the R/X diagram. Traditional distance relays and numerical relays that emulate the impedance elements of traditional relays do not measure absolute impedance.
They compare the measured fault voltage with a replica voltage derived from the fault current and the zone impedance setting to determine whether the fault is within zone or out-of-zone.
Impedance Characteristics
Relay measuring elements whose functionality is based on the comparison of two independent quantities are essentially either amplitude or phase comparators.
For the impedance elements of a distance relay, the quantities being compared are the voltage and current measured by the relay. There are numerous techniques available for performing the comparison, depending on the technology used. They vary from balanced-beam (amplitude comparison) and induction cup (phase comparison) electromagnetic relays, through diode and operational amplifier comparators in static-type distance relays, to digital sequence comparators in digital relays and to algorithms used in numerical relays.
Plain Impedance Characteristic
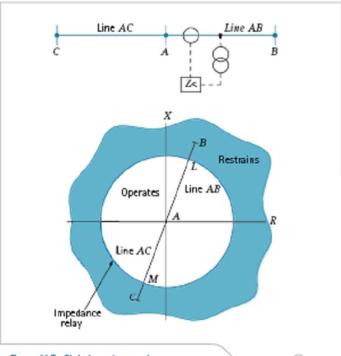
This characteristic takes no account of the phase angle between the current and the voltage applied to it; for this reason its impedance characteristic when plotted on an R/X diagram is a circle with its center at the origin of the co-ordinates and of radius equal to its setting in ohms.
Operation occurs for all impedance values less than the setting, that is, for all points within the circle. The relay characteristic, shown in Figure 11.7, is therefore non directional, and in this form would operate for all faults along the vector AL and also for all faults behind the Bus bars up to an impedance AM. It is to be noted that A is the relaying point and RAB is the angle by which the fault current lags the relay voltage for a fault on the line AB and RAC is the equivalent leading angle for a fault on line AC. Vector AB represents the impedance in front of the relay between the relaying point A and the end of line AB. Vector AC represents the impedance of line AC behind the relaying point. AL represents the reach of instantaneous Zone 1 protection, set to cover 80% to 85% of the protected line.
Disadvantages of Impedance Char.
A relay using this characteristic has three important disadvantages:
i. it is non-directional; it will see faults both in front of and behind the relaying point, and therefore requires a directional element to give it correct discrimination
ii. it has non-uniform fault resistance coverage
iii. it is susceptible to power swings and heavy loading of a long line, because of the large area covered by the impedance circle.
Impedance relay with Directional element
- Directional control is an essential discrimination quality for a distance relay, to make the relay non-responsive to faults outside the protected line. This can be obtained by the addition of a separate directional control element.
The impedance characteristic of a directional control element is a straight line on the R/X diagram, so the combined characteristic of the directional and impedance relays is the semi-circle APLQ shown in Figure below:
Mho Relay
The mho impedance element is generally known as such because its characteristic is a straight line on an admittance diagram. It cleverly combines the discriminating qualities of both reach control and directional control, thereby eliminating the ‘contact race’ problems that may be encountered with separate reach and directional control elements. This is achieved by the addition of a polarising signal. Mho impedance elements were particularly attractive for economic reasons where electromechanical relay elements were employed. As a result, they have been widely deployed worldwide for many years and their advantages and imitations are now well understood. For this reason they are still emulated in the algorithms of some modern numerical relays.
- The characteristic of a mho impedance element, when plotted on an R/X diagram, is a circle whose circumference passes through the origin, as illustrated in Figure (b).
This demonstrates that the impedance element is inherently directional and such that it will operate only for faults in the forward direction along line AB.
The impedance characteristic is adjusted by setting Zn, the impedance reach, along the diameter and ϕ, the angle of displacement of the diameter from the R axis. Angle ϕ is known as the Relay Characteristic Angle (RCA). The relay operates for values of fault impedance ZF within its characteristic.
Third zone and bus bar back-up zone
- In this application it is used in conjunction with mho measuring units as a fault detector and/or Zone 3 measuring unit. So, with the reverse reach arranged to extend into the busbar zone, as shown in Figure 11.10(a), it will provide back-up protection for busbar faults. This facility can also be provided with quadrilateral characteristics. A further benefit of the Zone 3 application is for Switch-on-to-Fault (SOTF) protection, where the Zone 3 time delay would be bypassed for a short period immediately following line energisation to allow rapid clearance of a fault anywhere along the protected line.
Quadrilateral Characteristic
- This form of polygonal impedance characteristic is shown in Figure 11.15. The characteristic is provided with forward reach and resistive reach settings that are independently adjustable. It therefore provides better resistive coverage than any mho-type characteristic for short lines. This is especially true for earth fault impedance measurement, where the arc resistances and fault resistance to earth contribute to the highest values of fault resistance. To avoid excessive errors in the zone reach accuracy, it is common to impose a maximum resistive reach in terms of the zone impedance reach.
Recommendations in this respect can usually be found in the appropriate relay manuals.
- Polygonal impedance characteristics are highly flexible in terms of fault impedance coverage for both phase and earth faults. For this reason, most digital and numerical distance relays now offer this form of characteristic.
Protection Features of Numerical Distance relays
Phase and earth fault distance protection, each with up to 5 independent
zones of protection. Standard and customised signalling schemes are available to give fast fault clearance for the whole of the protected line or cable.
> Directional earth fault protection (DEF)
- Undervoltage Protection
- Overvoltage Protection
- Directional or non-directional negative sequence overcurrent protection – This element can provide backup protection for many unbalanced fault conditions.
- Switch on to fault (SOTF) protection – These settings enhance the protection applied for manual circuit breaker closure.
- Trip on reclose (TOR) protection – These settings enhance the protection applied on auto reclosure of the circuit breaker.
- Power swing blocking – Selective blocking of distance protection zones ensures stability during the power swings experienced on sub-transmission and transmission systems.
Non-Protection Features
- Autoreclosure with Check synchronism ,
- Measurements – Selected measurement values polled at the line/cable terminal, available for display on the relay or accessed from the serial communications facility.
- Fault/Event/Disturbance Records – Available from the serial communications or on the relay display (fault and event records only).
- Distance to fault locator – Reading in km, miles or % of line length.
Quadrilateral Characteristic of Typical MICOM P444 Relay
Zones of Protection
Zone-1
The zone 1 elements of a distance relay should be set to cover as much of the protected line as possible, allowing instantaneous tripping for as many faults as possible. In most applications the zone 1 reach (Z1) should not be able to respond to faults beyond the protected line. For an underreaching application the zone 1 reach must therefore be set to account for any possible overreaching errors. These errors come from the relay, the VTs and CTs and inaccurate line impedance data. It is therefore recommended that the reach of the zone 1 distance elements is restricted to 80 – 85% of the protected line impedance (positive phase sequence line impedance), with zone 2 elements set to cover the final 20% of the line.
Here: Ra = Relay at bus A, Rb = Relay at bus B,
Z1 = Zone-1 Reach for Relay Ra = 80-85% Zab(Imp. Of Line AB),
Z2 = Zone-2 Reach for Relay Ra = 120% Zab or Zab+(< 50% Zbc),
Z3 = Zone-3 Reach for Relay Ra = 120%( Zab+Zbc),
Z4= Zone-4 Reach, reverse zone reach for relay Ra= 10-25% of Zab or
Z4 ≥ ((Remote zone 2 reach, Rb) x 120%) minus the protected line impedance
Zone-2
The zone 2 elements should be set to cover the 20% of the line not covered by zone 1. Allowing for underreaching errors, the zone 2 reach (Z2) should be set in excess of 120% of the protected line impedance for all fault conditions. Where aided tripping schemes are used, fast operation of the zone 2 elements is required. It is therefore beneficial to set zone 2 to reach as far as possible, such that faults on the protected line are well within reach. A constraining requirement is that, where possible, zone 2 does not reach beyond the zone 1 reach of adjacent line protection. Where this is not possible, it is necessary to time grade zone 2 elements of relays on adjacent lines.
For this reason the zone 2 reach should be set to cover ≤50% of the shortest adjacent line impedance, if possible. When setting zone 2 earth fault elements on parallel circuits, the effects of zero sequence mutual coupling will need to be accounted for.
The mutual coupling will result in the Zone 2 ground fault elements underreaching.
Zone-3
The zone 3 elements would usually be used to provide overall back-up protection for adjacent circuits. The zone 3 reach (Z3) is therefore set to approximately 120% of the combined impedance of the protected line plus the longest adjacent line. A higher apparent impedance of the adjacent line may need to be allowed where fault current can be fed from multiple sources or flow via parallel paths.
Zone-4
The zone 4 elements would typically provide back-up protection for the local busbar,where the offset reach is set to 25% of the zone 1 reach of the relay for short lines (<30km) or 10% of the zone 1 reach for long lines. Setting zone 4 in this way would also satisfy the requirements for Switch on to Fault, and Trip on Reclose protection, as described in later sections. Where zone 4 is used to provide reverse directional decisions for Blocking or Permissive Overreach schemes, zone 4 must reach further behind the relay than zone 2 for the remote relay. This can be achieved by setting:
Z4 ≥ ((Remote zone 2 reach) x 120%) minus the protected line impedance.
References : Areva Micom Numerical Relays